The Washington Post
For Barton Gellman, one of the reporters who handled the Snowden disclosures for The Washington Post, learning to use encryption tools only proved useful after much waiting. “I published my first PGP key in 2006,” Gellman said. “I was up and running with encryption and Tor for seven years before Edward Snowden found his way to my inbox. He could not have reached me if I had not left out the welcome mat.” Gellman now runs his own personal SecureDrop at the Century Foundation, but The Post itself was also an early adopter of SecureDrop, launching the system in June of 2014.
The Post appears to have developed an efficient system to monitor its SecureDrop. According to Steven Rich, a database editor for investigations at The Post, they have a team of three journalists who gather, assess, and distribute tips to reporters around the newsroom. Trevor Timm of the FPF even surmised that The Post may have the “best coordinated” system among all the organizations currently using SecureDrop.
“We spend a fair amount of time trying to figure out what something is and where it should go,” said Julie Tate, one of the journalists who monitors the SecureDrop at The Post. After delivering each tip, Tate and the other point people will respond to the source through the SecureDrop interface to let them know a reporter is looking into it. They also give some expectation of how further contact will be coordinated if the story moves forward.
“If I hook up a reporter with a source, often I’m not involved anymore—one hundred percent of the time I’m not involved anymore,” Tate said. “I’m like, this is what we’ve received, this is how this person can communicate with you—you know what I mean? It’s like introducing two people, and then I step out. I’m just facilitating people communicating with each other.”
When asked if SecureDrop has been successful at The Post, Tate replied, “Definitely. I can’t go into what those stories are. But we’ve had success with it, definitely.”
Rich said that interesting tips tend to receive about a week or two for pre-reporting before a full investigation is launched. “You don’t generally get entire stories leaked,” Rich said. “You get the tip of the iceberg.”
Rich also noted that most people in The Washington Post newsroom are aware of SecureDrop, but the majority don’t use it. Moreover, he said that many reporters mistakenly think they do not need it. “Most people work with more sensitive things than they think they do,” Rich explained.
Although the majority of the newsroom may not use SecureDrop, others are using tools like PGP instead. According to Tate, all of The Post’s foreign reporters use encryption tools of some kind. Data from the MIT key server reveals that the enrollment of Post reporters with encryption keys increased noticeably after the Snowden disclosures were published, while the installation of its SecureDrop system appears to have had little effect.
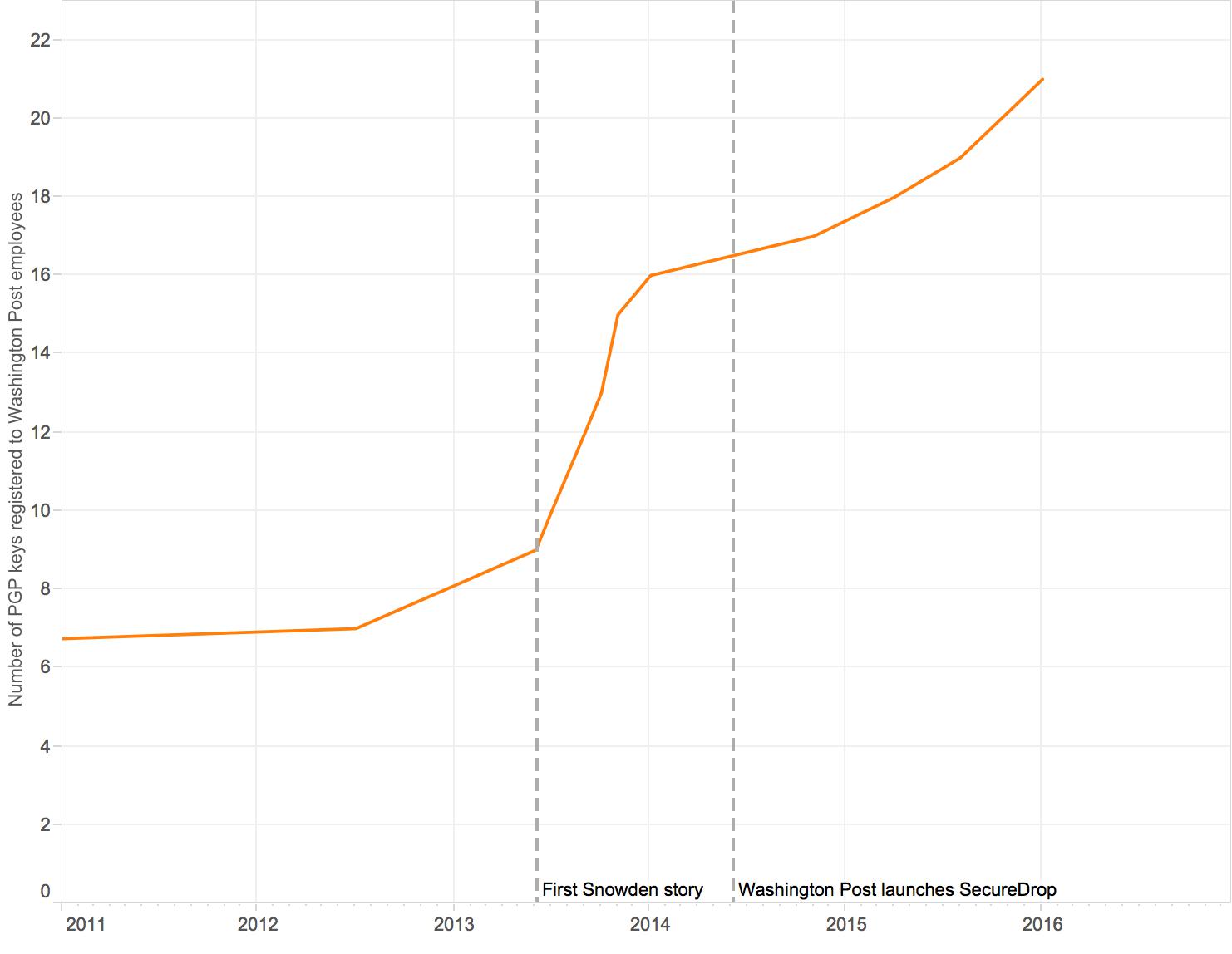 Number of public key registrations over time at The Washington Post.
Number of public key registrations over time at The Washington Post.