The Intercept
The Intercept is an online publication established in the wake of the Snowden disclosures by eBay founder Pierre Omidyar. Many of its current staff reporters and technologists were involved in reporting these disclosures, including Glenn Greenwald, Laura Poitras, and Micah Lee. Consequently, The Intercept is unique among news organizations in its focus on digital security, including mandatory training for its staff.
The organization’s concern for security is borne out by the large number of staff members enrolled on the MIT key server. The graph below shows the accumulated total registrations among employees of The Intercept and its parent company, First Look Media.
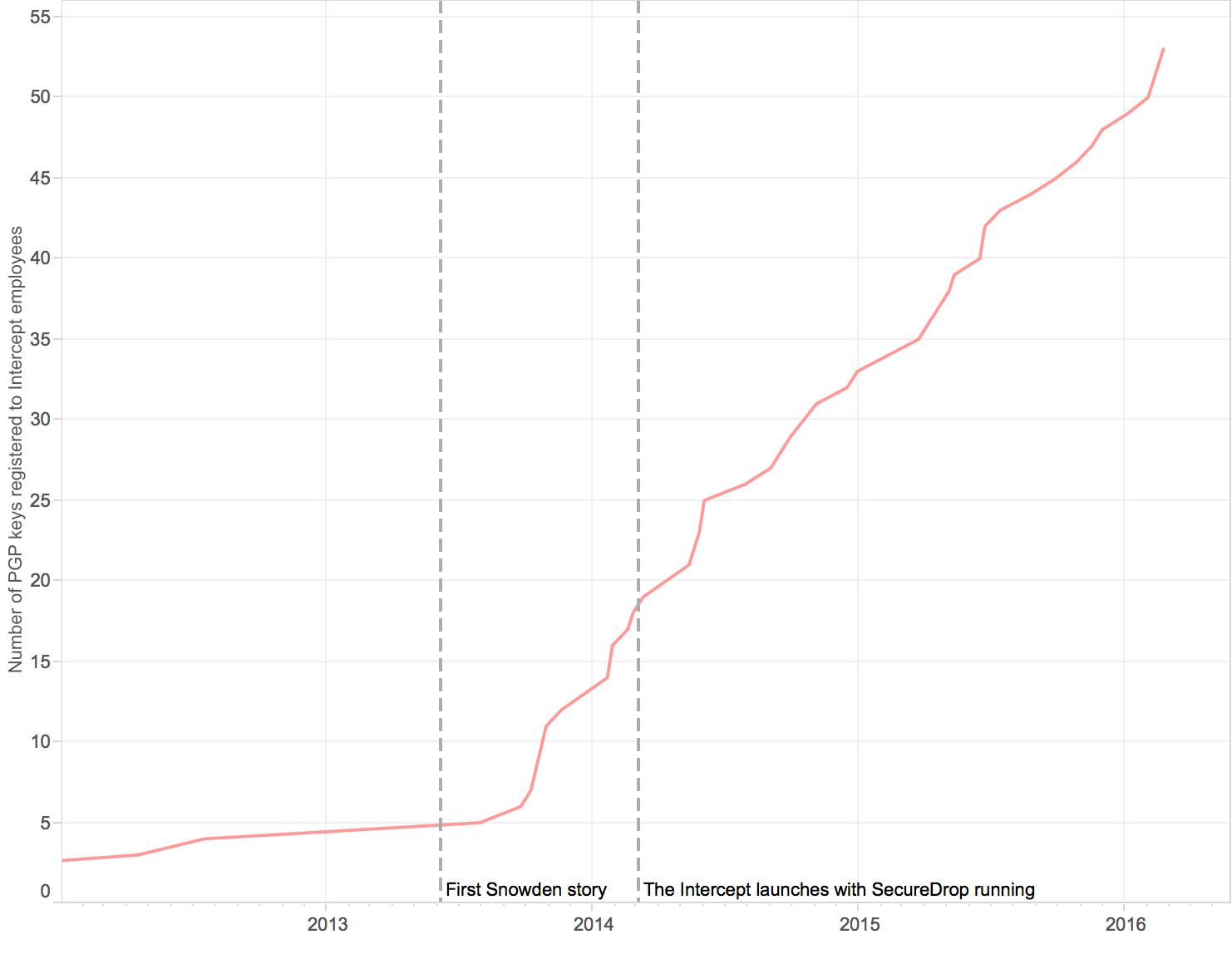 Number of public key registrations over time at The Intercept and First Look Media.
Number of public key registrations over time at The Intercept and First Look Media.
Beyond its large footprint on the MIT key directory, The Intercept is also notable because it launched in early 2014 with SecureDrop running from day one. Lee, one of the founders of the FPF and one of the developers of SecureDrop, not only set up The Intercept’s system, but was also the sole staff member checking it for some time.
Recently, a “centralized group” has joined Lee in reviewing submissions and distributing materials when a source is trying to contact a specific journalist. Betsy Reed, the editor of The Intercept, described this as a time-consuming but manageable process. “We had to get into a rhythm for checking the SecureDrop. It works best to do that on a rotating basis because there can be a high volume of material to get through, but we’ve gotten into that rhythm.”
Reed also confirmed that her organization has had an increasing level of success with SecureDrop. “Especially recently, as awareness grows of its existence, we’ve seen more and more good stories coming out of that pipeline,” she said, adding, “but as with any kind of tip line at any news organization, the vast majority of leads we get, they don’t pan out.”
Lee echoed that while The Intercept frequently receives tips and documents in its SecureDrop system and that a fair share of them warrant further reporting, they pass on the majority of material. “It’s very frequent that we get contacted through SecureDrop and the information we have is kind of interesting, and we talk about it for a while, but then we decide that it’s not interesting enough to warrant doing more journalism around it, or publishing anything,” he said. “Because, you know, most sources don’t have incredibly juicy stories for you. That’s pretty rare.”
Like other publications studied here, The Intercept does not make a practice of acknowledging when the source for a story contacted the outlet through SecureDrop. The first exception came in November 2015, when The Intercept published a story about a company called Securus that provides phone services to prisons. The journalism hook was that Securus was recording phone calls between inmates and their lawyers in violation of attorney-client privilege. The lede paragraph stated:
The materials—leaked via SecureDrop by an anonymous hacker who believes that Securus is violating the constitutional rights of inmates—comprise over 70 million records of phone calls, placed by prisoners to at least 37 states, in addition to links to downloadable recordings of the calls.11
Lee explained that the decision to reveal the use of SecureDrop in reporting the Securus story was the result of assessing the potential risk to the source, who dropped out of contact shortly after delivering the documents. “In this specific case, we looked into it and we couldn’t see any harm that could be done to our source, or our source’s identity, by saying that it came from SecureDrop. We don’t know the actual identity of our source, but we were able to validate the information.” Two weeks later, The Intercept posted a second story with direct acknowledgement that it was based upon documents sent through SecureDrop, but these acknowledgments are still rare.12
Reed underscored that these decisions are not specific to SecureDrop: “We have to evaluate the risks of disclosing any details about sourcing—including whether it comes via Securedrop—on a case by case basis, taking into account when possible the source’s assessment of their own risks, but also making our own independent assessment.”